OSCP Review & 2026 Preparation Guide
Table of Contents

OSCP vs. OSCP+: What Changed#
I took the OSCP in October 2024, weeks before OffSec launched OSCP+ on November 1, 2024.
| OSCP (what I took) | OSCP+ (Nov 2024 onward) | |
|---|---|---|
| Validity | Lifetime | OSCP+ expires every 3 years (underlying OSCP stays lifetime) |
| AD Set | Gated: compromise non-AD machine first | “Assumed compromise”: start with domain user |
| Bonus Points | 10 pts available | None, score entirely from exam |
| AD Scoring | All-or-nothing | Partial credit possible |
The PEN-200 course content and core methodology haven’t changed. This guide applies to both versions.
Pattern Recognition#
The OSCP isn’t about being smart. It’s about repetition until recognition becomes automatic.
Think about how radiologists train. They interpret thousands of studies until subtle abnormalities jump out.1 The OSCP is the same. You enumerate, exploit, and escalate so many times that when something looks off on the exam, you’ve seen it before. A service behaves strangely? Pattern matched.
But it’s not only pattern recognition. You develop a methodology. You look at what’s there, figure out what’s misconfigured, research whether the version you’re dealing with is vulnerable, check if there’s a public exploit on Google or GitHub. There’s a systematic process underneath the intuition. And through all of it, you’re asking yourself one question: what am I missing?
That combination — pattern recognition plus a repeatable process — is what actually gets you through the exam.
Prep#
- Won the voucher in 2020.
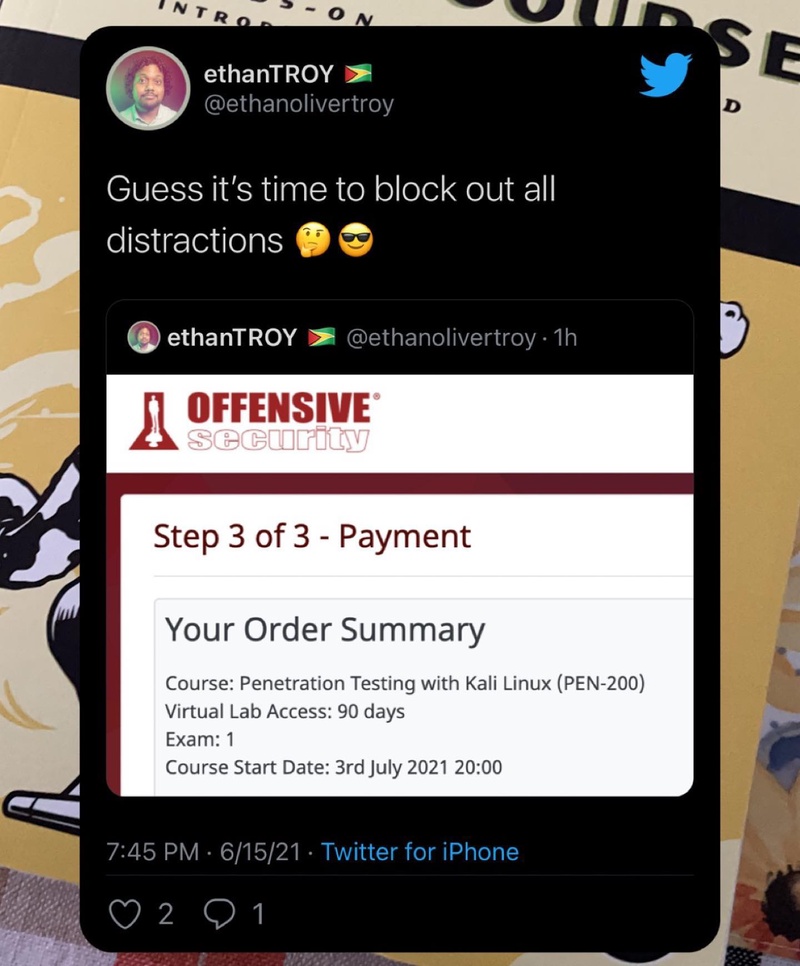
June 2021. Finally redeemed the voucher — PEN-200 with 90 days of lab access. - Life happened. Family medical emergencies, work.
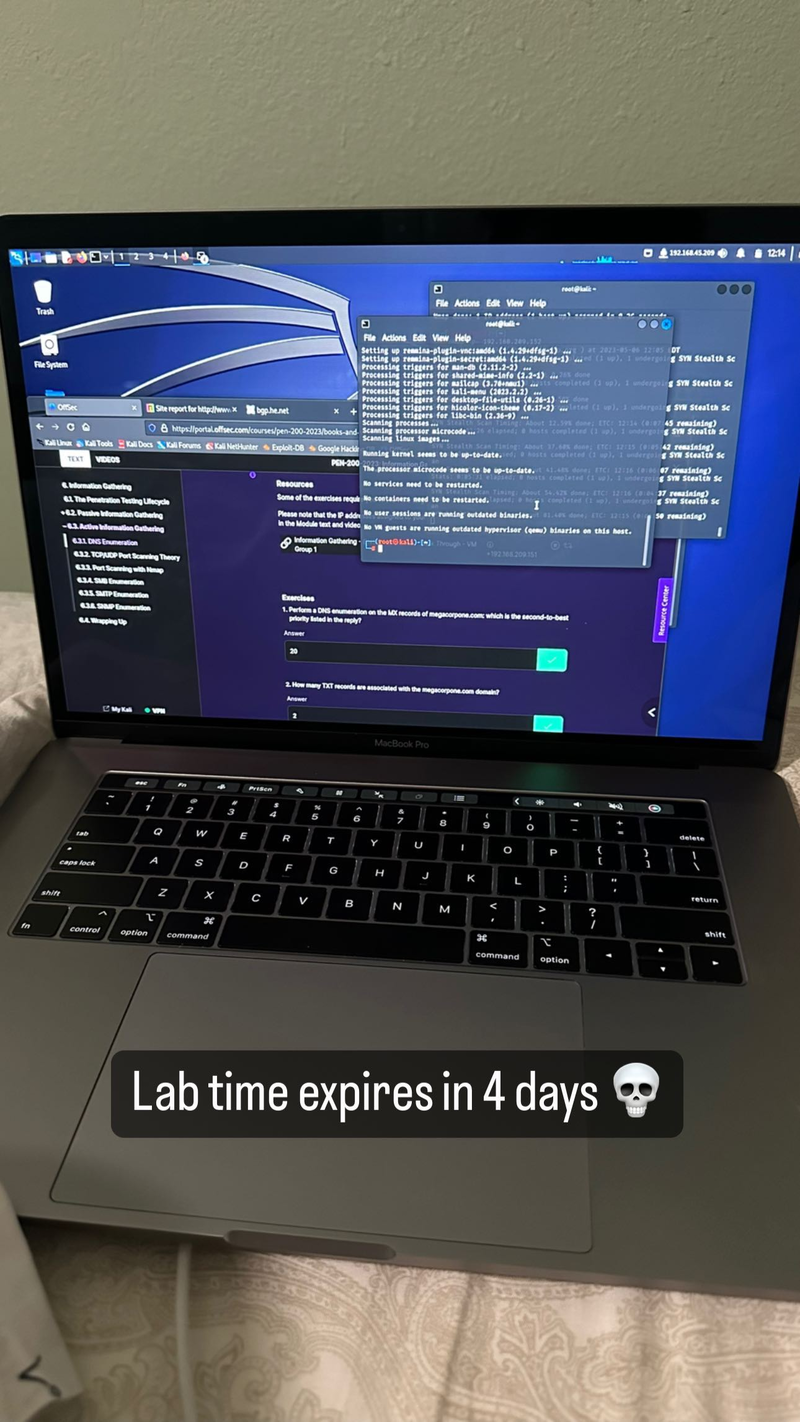
March 2023. Four days of lab time left. - It expired.
- Finally really committed in 2024, shored up weak Windows/AD skills with PNPT and CRTP, then ~2 months of grinding.
What I Used#
| Resource | Cost | Take |
|---|---|---|
| HTB Academy (Pen Tester path) | ~$18/mo | What I’d recommend starting with. Better than PWK, way cheaper. Feeds into CPTS cert. |
| PEN-200 | Included | Labs > PDF. I mostly skimmed the course material. |
| Proving Grounds | ~$20/mo | Most exam-like. Use in final weeks. |
| IppSec YouTube | Free | Taught me how to think about boxes. |
| HackTricks | Free | Kept open during every session and the exam. |
Your Notes Are Your Secret Weapon#
You can bring notes into the exam. Use that.
I documented every box in Obsidian. Markdown files, fast search, everything linked. By exam time, I had a searchable knowledge base of every technique, exploit, and edge case I’d encountered. When something looked familiar on the exam, I could pull up my notes from a similar box in seconds.
It became my second brain. Don’t overthink structure. Just write it down, tag it, and let Obsidian’s search do the rest.
The Exam#
23 hours 45 minutes. 3 standalone machines + 1 AD set (3 machines). 70 points to pass. Proctored via webcam.
| Target | Points |
|---|---|
| 3 Standalones | 20 each (10 user + 10 root) |
| AD Set | 40 |
| Pass | 70 |
The difficulty isn’t technical. It’s time pressure. With enough reps, nothing on the exam should surprise you. The 24-hour crunch is what makes it feel harder than it is.
The Grind#
- Enumerate everything in parallel. Scans run while you work.
- Bank points early. Knock out the easiest-looking machine first.
- Take breaks. Almost every breakthrough came after stepping away.
- Sleep if you need to. A rested brain finds more vulns they say. I only took a short nap though.
- Screenshot and document everything. Your future self will thank you during the report.
Should You Bother in 2026?#
Probably not. Unless someone else pays.
The OSCP used to be the pentesting cert. That era is over, I think. Cheaper options teach the same skills without the $1,749+ price tag and 3-year renewal cycle.
The cert landscape in 2026 isn’t what it used to be. OSCP was the golden ticket. Now there are dozens of comparable certs and platforms, and they’re all teaching the same skills for a fraction or competing the price.
If I were starting today with my own money: PNPT first for a solid offensive foundation, CRTP from Altered Security to get sharp on Active Directory, and CRTO from Zero Point Security because it’s genuinely fun and gives you hands-on time with real red team tooling. Grind HTB alongside all of it. I would only pursue OSCP+ if a job specifically requires it.
Course + exam runs $1,749. OSCP+ renewal is $799 or CPE every 3 years.
To be honest - I miss the try harder days.

To Marcus J. Carey: thank you. That giveaway changed my career trajectory.