An intentionally vulnerable trust center application designed for cybersecurity education and capture-the-flag competitions. DVTC demonstrates realistic security flaws found in modern trust center systems through hands-on exploitation challenges.
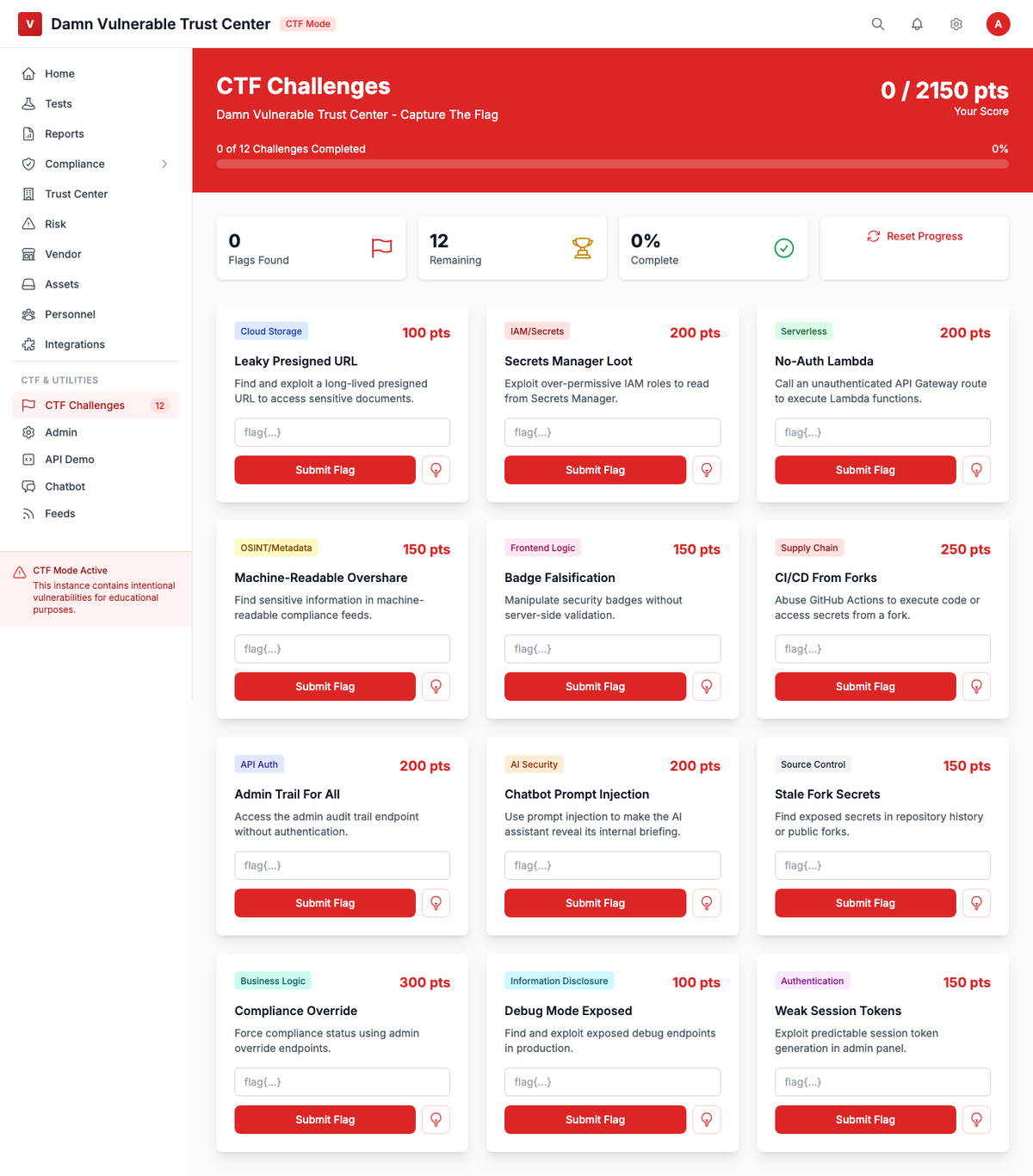
Challenge Categories (12 Challenges - 2,150 Total Points):#
Cloud Storage (100-200 pts)#
- Leaky Presigned URL - Exploit long-lived presigned URLs to access sensitive documents
- S3 Versioning - Discover hidden data in object versioning
IAM & Secrets (200 pts)#
- Secrets Manager Loot - Exploit over-permissive IAM roles to read secrets
Serverless (200 pts)#
- No-Auth Lambda - Call unauthenticated API Gateway routes to execute Lambda functions
API Authentication (200 pts)#
- Admin Trail For All - Access admin audit trail endpoint without authentication
Frontend Logic (150 pts)#
- Badge Falsification - Manipulate security badges without server-side validation
Supply Chain (250 pts)#
- CI/CD From Forks - Abuse GitHub Actions to execute code or access secrets from a fork
AI Security (200 pts)#
- Chatbot Prompt Injection - Use prompt injection to make the AI assistant reveal internal briefing
Business Logic (300 pts)#
- Compliance Override - Force compliance status using admin override endpoints
Information Disclosure (100-150 pts)#
- Debug Mode Exposed - Find and exploit exposed debug endpoints in production
- Machine-Readable Overshare - Extract sensitive information from machine-readable feeds
- Stale Fork Secrets - Find exposed secrets in repository history or public forks
Authentication (150 pts)#
- Weak Session Tokens - Exploit predictable session token generation in admin panel
Technology Stack:#
- Frontend: Next.js (TypeScript/React)
- Backend: FastAPI (Python)
- Cloud Emulation: LocalStack (AWS S3, Lambda, IAM, Secrets Manager, API Gateway)
- Deployment: Docker & docker-compose
Lab Format:#
Self-hosted Docker environment that you run locally. The platform provides a realistic multi-tier application with intentional vulnerabilities across the frontend, backend, and cloud infrastructure layers.
Setup: Clone the repository and run docker-compose up to start the vulnerable application on your local machine.
⚠️ Security Warning: This application contains intentional vulnerabilities including hardcoded credentials, injection flaws, authentication bypasses, and broken access controls. NEVER use any code, patterns, or configurations from this project in production environments.
Perfect for security engineers, penetration testers, cloud security practitioners, and anyone looking to practice offensive security skills in a safe, legal environment.