Why GRC Engineering?#
“The technology has always been there, so I often ask—why are we still doing things this way?”
Traditional GRC workflows are painfully manual. Analysts spend hours hunting through file shares, pulling screenshots, exporting logs, and mapping everything back to control requirements. It’s tedious, repetitive, and exactly the kind of work that should be automated.
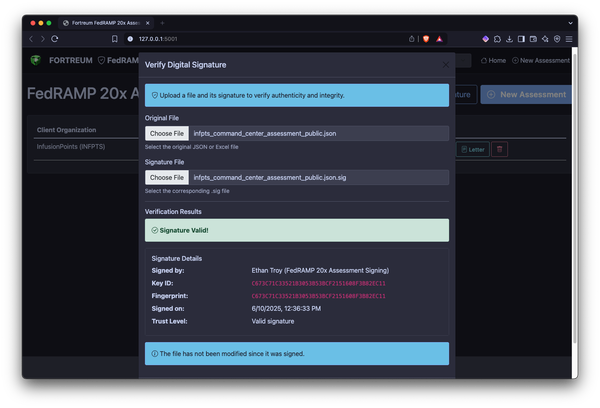
GRC Engineering treats compliance like any other engineering problem. Instead of clicking through consoles and pasting screenshots into Word docs, you write scripts that query APIs directly, validate configurations programmatically, and generate evidence automatically. The output is the same—proof that controls are in place—but the process is repeatable, version-controlled, and fast.
Multi-Cloud Reality#
“Building checks that work across AWS, Azure, and GCP means abstracting away the differences while capturing what matters.”
Most organizations aren’t single-cloud. They have workloads spread across AWS, Azure, GCP, and sometimes on-prem. Each provider has different APIs, different naming conventions, and different ways of surfacing security configurations.
The key is finding common abstractions. Identity policies, network controls, encryption settings—these exist everywhere, just behind different API calls. Once you map those abstractions, your compliance checks become portable. A control validation written for AWS IAM can inform how you check Azure AD or GCP IAM.
Open Source Approach#
“Everything can be done with either a PowerShell script, a Python script, command line… some kind of lambda.”
You don’t need expensive commercial tools to automate GRC. The primitives are simple:
- API access to your cloud providers (AWS CLI, Azure CLI, gcloud)
- Scripting to query and validate configurations (Python, Go, Bash)
- Scheduling to run checks continuously (cron, GitHub Actions, Cloud Functions)
- Reporting to surface findings (JSON, markdown, dashboards)
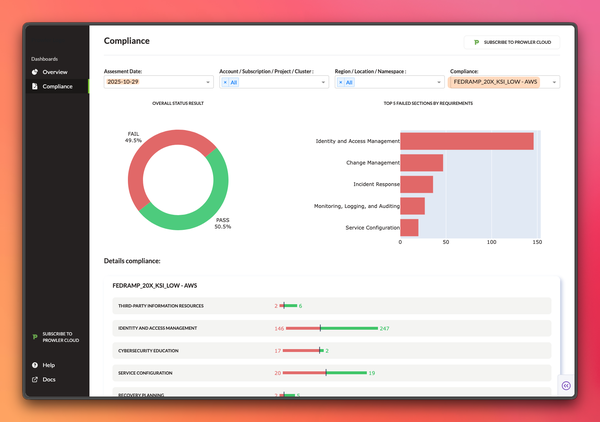
Open source tools like Prowler, ScoutSuite, and Steampipe provide solid foundations. But sometimes the best solution is a custom script that does exactly what you need for your specific control mapping.
Practical Takeaways#
Attendees walked away with:
- Actionable techniques to reduce manual compliance work
- Code examples for multi-cloud evidence collection
- Integration patterns for connecting compliance checks to existing pipelines
- Mental models for thinking about GRC as an engineering discipline
The goal isn’t to eliminate human judgment—it’s to automate the grunt work so humans can focus on actual security decisions.
Resources#
- BSides Orlando 2025
- Sessionize Talk Page
- FedRAMP TUI - Terminal UI for exploring FedRAMP data
- CMVP TUI - Terminal UI for NIST cryptographic module validation
- I Built a GRC Agent for $10 - Related post on AI-powered GRC automation