An Injection of Documentation Context into Workflows#
FedRAMP 20X has pushed a lot more structured data into the official GitHub repo which means we can stop opening PDFs and start asking questions…maybe? This project is a simple documentation server that pulls raw text and JSON from FedRAMP’s repo, indexes it, and exposes it via an MCP so tools can search and reason over the source material. For a long time, interpretation of confusing compliance documents was done by GRC incumbents that made an entire career on reading and interpreting these docs. But in 2025, virtually everyone is dropping PDFs into ChatGPT, Claude, or Notebook LLM and telling their AI assistant to “explain this to me like I’m five.” A documentation MCP server could help structure that process more formally by allowing agents to query the source material directly rather than relying on RAG or ad-hoc document uploads. This implemnentation isn’t so much about adding too many new tools as it is about injecting relevant context into existing AI workflows.
Architecture#
flowchart TD
subgraph Sources["Data Sources"]
A[FedRAMP/docs Repo]
B[FRMR Documents]
C[KSI Definitions]
D[Control Mappings]
end
subgraph Server["MCP Server - TypeScript"]
E[ensureRepoReady]
F[buildIndex]
G[StdioServerTransport]
end
subgraph Tools["23 MCP Tools"]
subgraph DocTools["Document Discovery"]
H1[listFrmrDocuments]
H2[getFrmrDocument]
H3[listVersions]
end
subgraph KSITools["KSI Operations"]
I1[listKsi]
I2[getKsi]
I3[filterByImpact]
end
subgraph ControlTools["Control Mapping"]
J1[listControls]
J2[getControlRequirements]
J3[analyzeControlCoverage]
end
subgraph SearchTools["Search & Analysis"]
K1[searchMarkdown]
K2[searchDefinitions]
K3[diffFrmr]
end
end
subgraph Clients["AI Clients"]
L[Claude Desktop]
M[Cursor]
N[Claude Code]
end
A --> E
B & C & D --> E
E --> F
F --> G
G --> DocTools & KSITools & ControlTools & SearchTools
DocTools & KSITools & ControlTools & SearchTools --> L & M & N
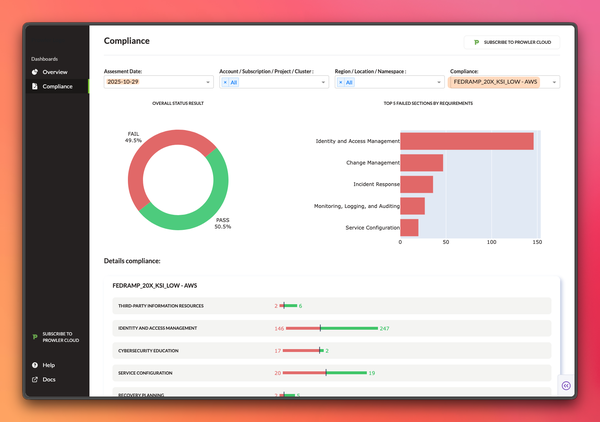
The server is built in TypeScript using the Model Context Protocol specification. On startup, it clones or updates the FedRAMP/docs repository locally, then builds a searchable index of all content. The server exposes 23 tools organized into four categories: document discovery (list and retrieve FRMR docs), KSI operations (query Key Security Indicators by impact level), control mapping (analyze SP 800-53 coverage), and search/analysis (grep controls, diff versions, find definitions). AI clients like Claude Desktop, Cursor, or Claude Code connect via stdio transport and can call any of these tools directly.
I’ve been experimenting with documentation-based MCPs and the results are mixed. For a deeper dive into MCP’s limitations, see The Problems with Model Context Protocol.
What’s New in v0.2.1#
The project has seen significant updates to align with FedRAMP 20x changes:
Evidence Examples Tool - The get_evidence_examples tool now provides automation-friendly suggestions for compliance evidence across 72 KSI indicators. It covers 463 documentation URLs across 11 major FedRAMP marketplace services including AWS, Azure, GCP, Google Workspace, Microsoft 365, Okta, CrowdStrike, and Sumo Logic.
Health Check with Repo Metadata - The health check tool now returns repository commit hash, date, and auto-update configuration status so you can verify documentation freshness.
Claude Code Plugin - Includes slash commands and agent skills for specialized compliance analysis workflows. Supports both CLI commands and .mcp.json project-scoped configuration for team collaboration.
Security-Hardened Docker - The container now runs as a non-root user with read-only filesystem, dropped capabilities, and memory constraints following 2025 MCP security best practices.
Auto-Update Functionality - Built-in update checking (configurable every 24 hours) keeps FedRAMP data current without manual intervention.
FedRAMP 25.12A Support - Handles 4 retired KSIs per the latest FedRAMP release while preserving backward compatibility.